The January 2024 Akira ransomware attack on Finnish IT company Tietoevry’s Swedish data centers in January and the resultant Internet outages underscore the importance of insight into upcoming threats, and the challenges of identifying and defending against them.
As part of their attack, the Akira operators exploited CVE-2023-20269, a vulnerability in the remote access VPN component of Cisco’s Adaptive Security Appliance and Firepower Threat Defense software. Akira’s choice of technique was not without precedent as exploiting security software to enable an attack is not new. A recent example is the GuptiMiner deployment through hijacking the update process of eScan antivirus.
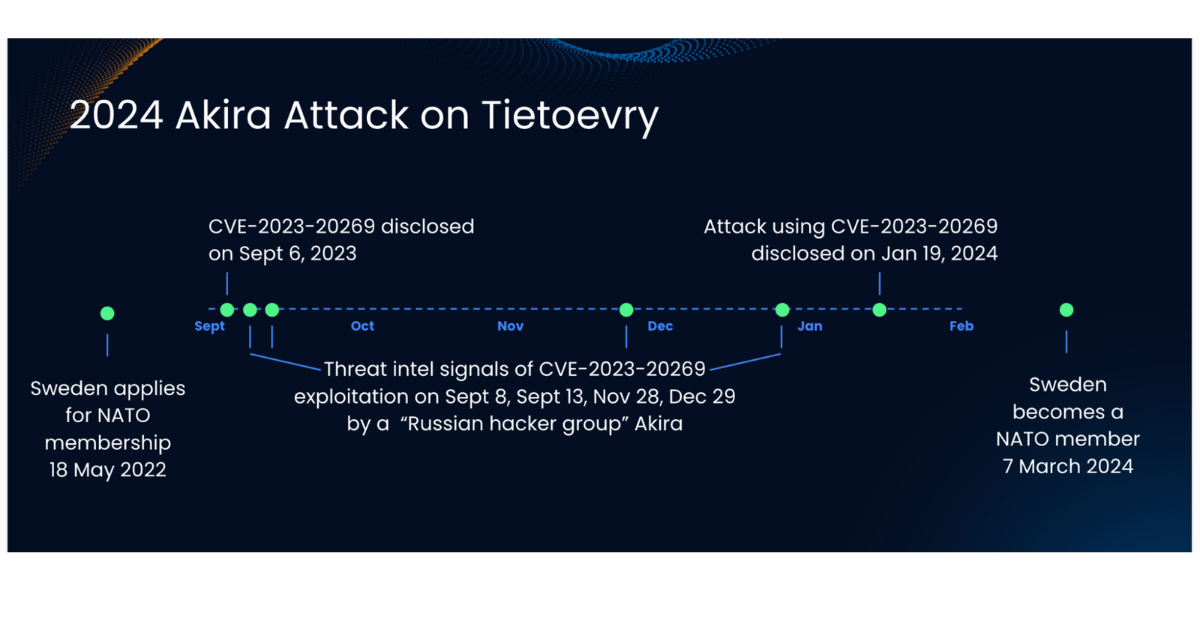
Tietoevry was hit by Akira on January 19, 2024. CVE-2023-20269 was disclosed by Cisco on September 6, 2023, fully patched on October 11, 2023, and was added to the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerability (KEV) list on November 13, 2023, a full two months before Tietoevry was attacked. SixMap threat intelligence identified multiple cases of exploitation of CVE-2023-20269 in the months before the Tietoevry attack, with the first detections of increased targeting of Cisco ASA appliances in March of 2023 through August 2023 before the Cisco disclosure of the vulnerability on September 6, 2023.
Following that disclosure, SixMap threat intelligence found reports of exploitation from September 8, 2023, September 13, 2023, September 14, 2023, October 4, 2023, November 28, 2023, December 21, 2023, and December 31, 2023.
Akira, a relatively new ransomware group, was first identified in attacks starting in March of 2023, with no apparent relation to the previous ransomware of the same name which was active from 2017 to 2021. The modern Akira’s attack methodology has been noted to have similarities to the Conti ransomware group that dissolved in May 2022, including its encryption binary sharing string obfuscation techniques, and its file exclusion list being an exact match. Microsoft states that Akira is not openly-sold as Ransomware as a Service (RaaS) but instead operates as a closed-group. It is also believed to be Russian in origin by both the Swedish government and due to its significant overlap with Conti, which also allegedly had ties to the Russian Federal Security Service (FSB).
SixMap advocates a threat actor and Ransomware-first approach to vulnerability prioritization as well as an evaluation of a vulnerability’s EPSS rating, rather than relying on CVE scoring. The threat from CVE-2023-20269 was scored at a base 5.0, or medium severity. However, data from SixMap and partners detected increased targeting of Cisco ASA VPN appliances by a threat actor inMarch of 2023, and documented specific use by Akira as early as September 8, 2023. Notably, Lockbit ransomware was also documented using the same vulnerability on the same date.
Further exploitation of this CVE by Akira was documented November 28, 2023 and December 21, 2023, both indicators that proactive defense to remediate the flaw was necessary due to the continued pattern of exploitation by cybercriminals. Even more notably, the Finnish National Cyber Security Center warned of specific attacks on Cisco VPN vulnerabilities on December 14, over a month before the Tietoevry attack, and again on January 15, 4 days before the attack on Tietoevry in Sweden.
Exploitation of CVE-2023-20269 allows remote, unauthenticated attackers to brute force valid username/password combinations, or allows authenticated remote attackers to establish a VPN session with an unauthorized user. While the vulnerability itself doesn’t allow an attacker to bypass authentication, the attacker could authenticate by gaining valid credentials if no multi-factor authentication (MFA) system was in place, or if that system itself is vulnerable.
The two-day turnaround between Cisco’s disclosure of the vulnerability of their VPN appliances and the documented exploitation by Akira demonstrates the speed that threat actors work with and the need to be able to proactively work to defend vulnerable systems within the shrinking window between disclosure and exploitation. While no patch was available, Cisco issued temporary workaround fixes, including consecutive login failure lockouts to counter brute-forcing attacks and denying user access to vulnerable connection profiles until the patch was released.
Since March of last year, Akira ransomware operators have compromised approximately 250 entities worldwide and grossed around $42 million in ransom payments, having an undeniable impact on organizations across multiple industries, including finance, education, and real estate.
Specifically in Finland, the Finnish National Cyber Security Center (NCSC), reported 12 Akira ransomware attacks targeted businesses in 2023 and were “particularly related to weakly secured Cisco VPN implementations or their unpatched vulnerabilities” with a usually difficult recovery.
The group’s successful encryption of Tietoevery’s virtualization and management servers resulted in staff at the majority of Sweden’s universities and more than 30 government agencies losing the ability to submit personal leave or expense requests through Primula, a widely used payroll and HR company. There were also initial concerns that personal information from 120 government employees might have been leaked, however, later findings showed no personal information was ultimately compromised. Also affected were discount retail chain Rusta, construction raw materials supplier Moelven and agricultural supplier Granngården, who were forced to temporarily close stores while waiting for IT services to be restored. In total, estimations for the financial impact suggest it may have cost at least SEK 1.2 billion.
Following the attack, the Swedish Parliament, itself a secondary victim of the Akira attack, held a seminar on the topic of Russian cyberattacks. Finland and Sweden both sparked Russian ire through their accession to the North Atlantic Treaty Organization (NATO) on April 4, 2023 and March 7, 2024, respectively, though their process of joining started as part of a broader international and geopolitical realignment following the Russian invasion of Ukraine in February of 2022.
Sweden has a history of facing cyberattacks from Russia, with the head of the Swedish Military Intelligence and Security Service (Must) telling Sveriges Television (SVT) in 2016 that Russia is the biggest source of cyberattacks on the country.
In a similar, though larger-scale attack, the 2017 breach of Equifax consumer data was enabled similarly to the attack on Tietoevry. Equifax had a known Apache Struts vulnerability (CVE-2017-5638) in its online credit dispute portal. While the patch had been issued March 6, two months before the breach, Equifax had not yet updated the system to eliminate that vulnerability, not because they failed to patch any software, but because of a lack of visibility into all instances of it on their network. Exploitation of the vulnerability by cybercriminals was documented as early as March 9. Instead, the attackers scanning Equifax’s systems were the ones to discover that the software was vulnerable in an Atlanta, Georgia-area server and used it to conduct the attack. Analysis of the Equifax breach had other experts arguing the value of visibility in corporate networks, on the principle of knowing what software is running to know what is vulnerable.
Overall, the impact of the Akira attack on Tietoevry highlights the importance of real-time updated knowledge of both threats and vulnerabilities. SixMap works on behalf of clients to discover all Internet-facing assets across IPv4 and IP6 and identifies threats as they are first reported. Using proprietary and open-source threat intelligence, SixMap prioritizes and validates the most imminent threats, enabling swift action so that organizations can operate at the speed of threats.